CORPORATE OVERVIEW
Simplifying Enterprise Security
The Scary Big Picture
Nobody is exception for cyber attacks
% of companies that got hacked globally in 2020
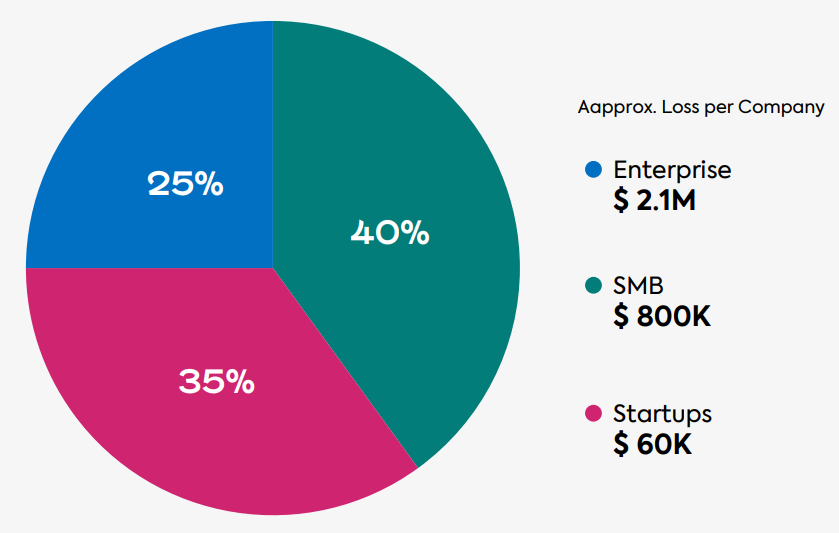
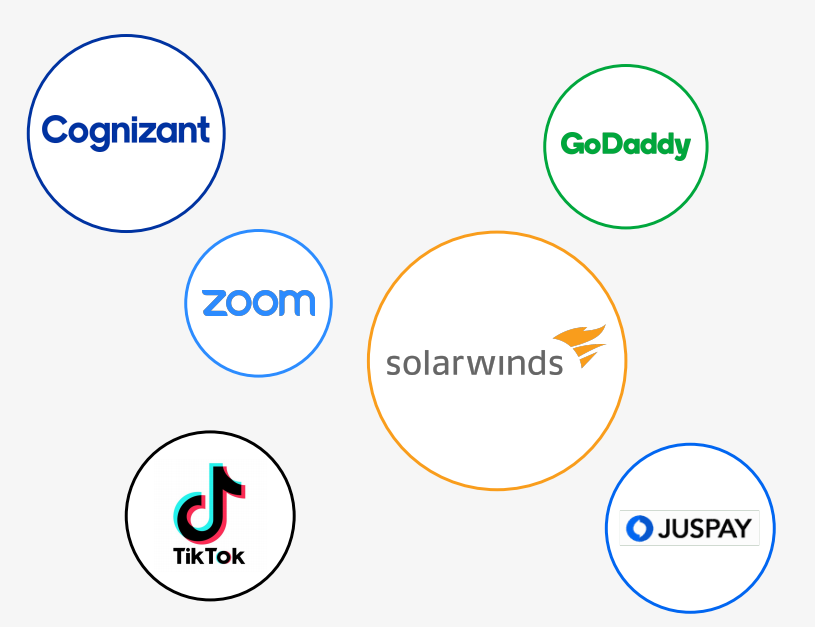
Companies that got hacked in 2020
By failing to prepare, you are preparing to fail
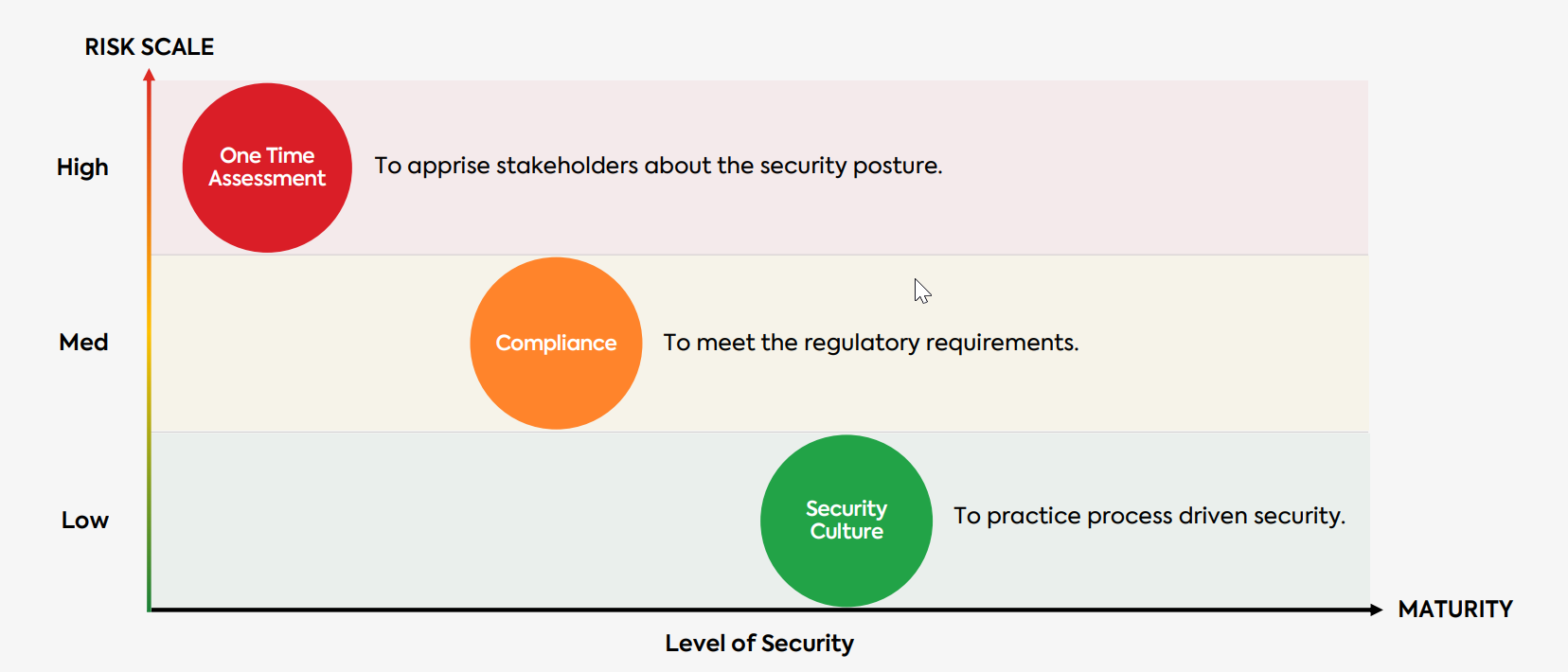
Objective Behind Security Assessment
Application Security
Gain in-depth insight into your application security
| MATURITY | Level 1 VAPT 




|
Level 2 Secure Code Review 




|
Level 3 Security Automation 




|
|---|---|---|---|
| Objective | Discover vulnerabilities quickly in external and internal applications | Identify, evaluate and improve coding practices | Continuous security at the speed of DevOps |
| What you get? | Automated & manual testing with focus on business logic issues | Automated and manual review with focus on security issues in architecture, design and 3rd party libraries | Implementation of DevSecOps |
| Delivery Time | ~ 2 to 3 weeks | ~3 to 4 weeks | ~5 to 6 weeks |
| Deliverables | • VAPT Report • Mitigation Support • Retesting (2 times) • Product Statement • Certificate of Security |
• Review Report • Training Developers* • Mitigation Support • Revalidation (2 times) |
• Deployment of in-house & open-source products • Assessment report on every major release • Setting up an application security automation process |
Network Security
Protect your networks inside and out
| Network VAPT |
Configuration Review |
AD Pentest |
Wireless Pentesting |
VoIP Pentesting |
|
|---|---|---|---|---|---|
| Objective | Protect your network from internal and external threat actors | Review configuration for potential security gaps | Ensure your AD is securely configured | Regulate your wireless network security posture | Protect your VoIP devices |
| What you get? | Blackbox assessment from hacker’s perspective | Whitebox assessment to discover misconfigurations | Assessment of Active Directory for misconfigurations | Audit the wireless nodes from hacker’s perspective | Assessment of VoIP application and devices |
| Delivery Time | ~ 2 to 3 weeks | ~ 2 to 3 weeks | ~5 to 7 weeks | ~ 2 to 3 weeks | ~ 2 to 3 weeks |
| Deliverables |
• VAPT or Review Report • Mitigation Support • Retesting (2 times) |
||||
Cloud Security
Cloud Security is a shared responsibility
| Cloud Pentesting | Cloud Infra Review | Cloud Monitoring | |
|---|---|---|---|
| Objective | Ensure your cloud networks are safe and secure | Ensure your app services are runningin safe environment | Respond to your cloud threats in real-time |
| What you get? | Assess your public and privateinstance on cloud | Auditing your cloud environmentfor security misconfigurations | Equip yourself with incident response capabilities |
| Support for | AWS, Azure, GCP & more | AWS, Azure, GCP & more | AWS |
| Delivery Time | ~ 2 to 3 weeks | ~1 to 2 weeks | ~3 to 4 weeks |
| Deliverables | • Review Report • Mitigation Support • Retesting (2 times) • Certificate of Security |
• Review Report • Mitigation Support • Retesting (2 times) • Certificate of Security |
• Deploying in-house product • 8x5 or 24x7 SOC Analysts • Extensive Support |
Threat Simulation
How prepared are you to handle a cyber attack?
| Red Team Assessment | Red Team vs Blue Team | Social Engineering Assessment | |
|---|---|---|---|
| Objective | Simulate real-world cyber attacks on your enterprise | Evaluate the effectiveness of your defences | Test your employees’ current state of phishing awareness |
| People, process, and technology in-scope | Identify how well equipped your SOC team is | Evaluate business risk if a phishing attack is successful | |
| Objective driven exercise to discover highly critical entry and pivot points | Uncover mishaps in your SIEM and its efficiency | Validate your email security controls | |
| Delivery Time | ~ 4 to 6 weeks | ~5 to 7 weeks | ~ 4 to 6 weeks |
| Deliverables |
• Review Report • Executive Report |
• Review Report • Executive Report |
• Review Report • Executive Report |
Compliance & Auditing
Adhere to compliances regulators guidelines
| ISO 27001 For any organization |
PCI DSS For Fintech |
HIPAA For Healthcare |
GDPR For EU userbase |
SOC Type 2 For SaaS Companies |
|
|---|---|---|---|---|---|
| What you get? | • Perform gap analysis • Domain specific security audit • Implement regulatory controls • Perform pre-audit checks • Certification |
||||
| Delivery Time | ~ 15 to 17 weeks | ||||
| Deliverables | • Audit Report • Review Report • Executive Report • Certification and Training |
||||